Multi-Account Configuration Management In AWS
GitOps-driven SSM Parameter Store automation for secure, scalable configuration management across multiple AWS accounts
The Challenge
Managing application configuration across multiple AWS accounts in a large enterprise environment presented significant challenges:
- Manual Configuration Updates: Teams were manually updating SSM parameters across 6+ AWS accounts
- Inconsistent Deployments: Configuration drift between environments led to deployment failures and application testing inconsistency
- Security Concerns: No audit trail for configuration changes and potential exposure of sensitive data (without relying heavily on AWS tools)
- Time Inefficiency: Configuration updates took tedious amounts of time
Solution Architecture
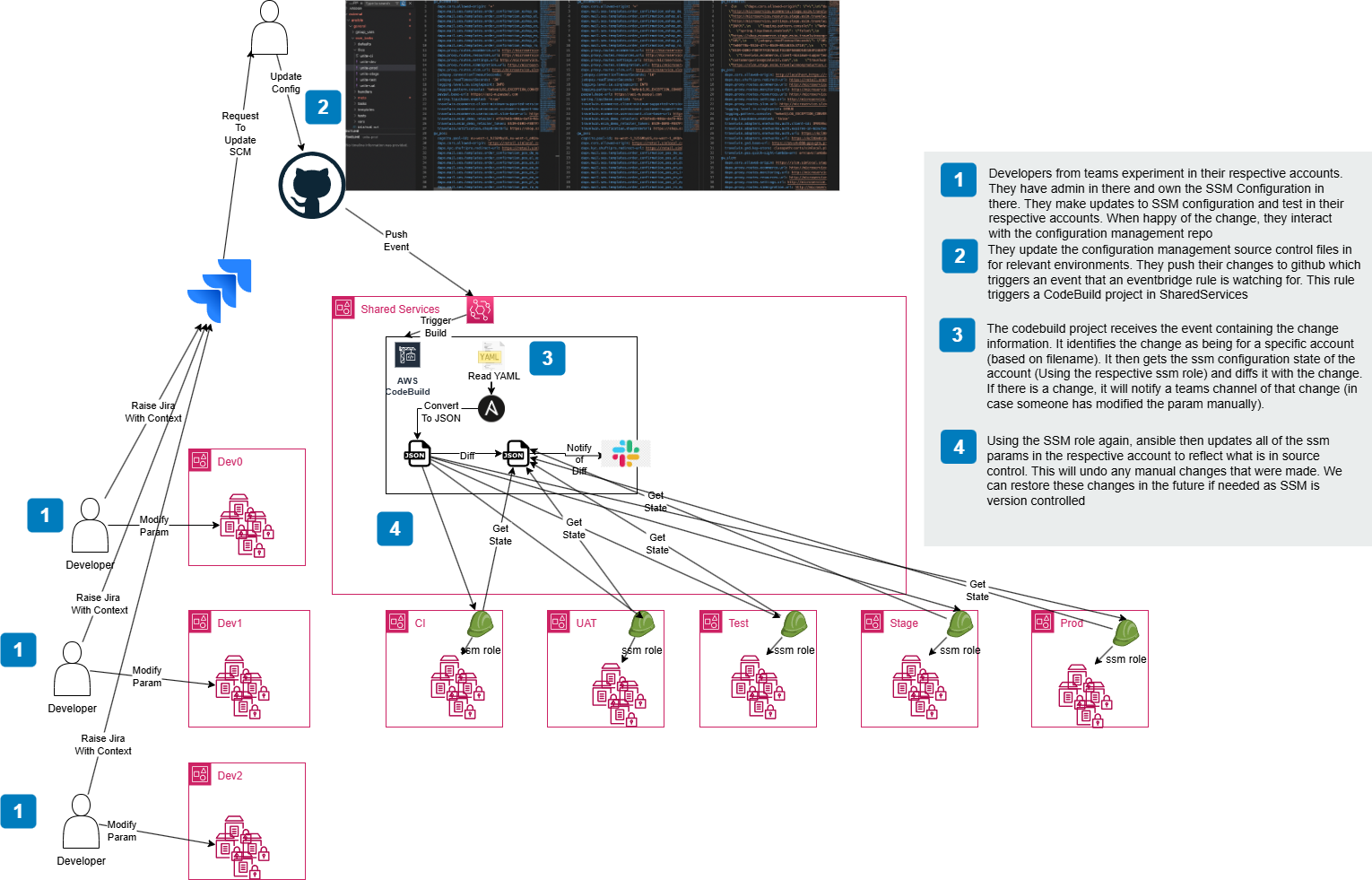
GitOps-Driven Configuration Pipeline
The solution implements a fully automated, GitOps-driven approach to configuration management using YAML-based configuration files stored in a GitHub repository.
1. YAML Configuration Management
Configuration stored as YAML files in GitHub with environment-specific overrides and validation schemas.
2. Automated CI/CD Pipeline
GitHub Webhooks trigger AWS CodeBuild jobs that process YAML files and update SSM parameters across target accounts.
3. Cross-Account Access
IAM roles with least-privilege access enable secure parameter updates across multiple AWS accounts.
4. Ansible Automation
Ansible playbooks orchestrate the deployment process with error handling.
Implementation Details
YAML Configuration Structure
Designed a hierarchical YAML structure supporting environment inheritance and parameter encryption.
# environments/production/app-config.yml
environments:
production:
database:
host: !encrypted "AQICAHi..."
port: 5432
name: "prod_app_db"
api:
base_url: "https://api.prod.company.com"
timeout: 30
features:
new_dashboard: trueGitHub Actions Workflow
Implemented GitHub Actions that validate YAML, trigger CodeBuild, and provide deployment status.
name: Deploy Configuration
on:
push:
branches: [main]
paths: ['environments/**/*.yml']
jobs:
deploy:
runs-on: ubuntu-latest
steps:
- name: Validate YAML
run: yamllint environments/
- name: Trigger CodeBuild
run: aws codebuild start-build --project-name config-deployerAnsible Playbook Orchestration
Created modular Ansible playbooks for parameter deployment with comprehensive error handling.
- name: Deploy SSM Parameters
hosts: localhost
tasks:
- name: Process configuration files
include_tasks: process_config.yml
vars:
environment: "{{ target_env }}"
account_id: "{{ target_account }}"
- name: Update SSM parameters
amazon.aws.aws_ssm_parameter_store:
name: "{{ item.key }}"
value: "{{ item.value }}"
type: "{{ item.type | default('String') }}"
loop: "{{ processed_params }}"Key Features
Secure by Design
Encrypted sensitive parameters using AWS KMS with role-based access control and audit logging.
Automated Validation
YAML schema validation and configuration drift detection prevent deployment errors.
Environment Inheritance
Base configurations with environment-specific overrides reduce duplication and errors.
Rollback Capability
Git-based versioning enables instant rollbacks to previous configuration states.
Audit Trail
Complete audit trail of configuration changes with GitHub commit history and CloudTrail logs.
Multi-Account Support
Seamless deployment across multiple AWS accounts with cross-account IAM roles.
Results & Impact
Business Benefits
- Operational Efficiency: Development teams can focus on feature development instead of configuration management
- Risk Reduction: Eliminated configuration drift and manual errors that previously caused production incidents
- Compliance: Automated audit trail satisfies regulatory requirements for change management
- Scalability: Solution easily extended to new AWS accounts and environments
- Developer Experience: Simple YAML-based configuration updates through familiar Git workflows